To influence present tech-savvy shoppers, you should prefer online sales marketing to expand your customer base and increase your revenue. E-commerce sector continues to grow with each passing year—and there’s no chance that its popularity will decrease at any time. Get in on this business growth potential by enabling your consumers to purchase your goods or services online. At the same time, you should also keep a vigil eye on the new security problems and risks that may arise with an online business. You should always keep security as your topmost priority when selling online. Customers are extremely cautious of…
Continue Readingcybersecurity
SSO – Everything at just a single click
Single sign-on (SSO) is a user authentication service which enables the user to access several numbers of applications at just one set of login credentials such as name and password. In a fundamental web SSO administration, an agent module on the application server recovers the particular authentication credentials for an individual from a devoted SSO arrangement server while confirming the client against a client store, for instance- a lightweight directory access protocol (LDAP) index. The administration confirms the end client for each one of the applications the client has been offered rights to and disposes of future password prompts for…
Continue ReadingA Year With a Zero-Day
You might be wondering what you never had heard of zero-day any before. Is it real or not that a year has zero-day? Well to break the surprise… It is not any day in a year rather it’s a flaw in the software, hardware, or firmware. Zero-day is referred to an attack which has zero days between the discovery of a vulnerability and the first attack. That means when a zero-day vulnerability is made public, it is known as n-day or one-day vulnerability. Some zero-day attacks are attributed to APT actors (advanced persistent threat), hacking, or cybercrime groups connected to…
Continue ReadingUnsuspectable BOTNET
A botnet is a collection of internet-connected devices, each of which is running one or more bots. A bot can be PC, servers, mobiles, and internet of things devices which are infected and controlled by common malware. A botnet is the combination of ‘robot’ and ‘network’ and is used with a malicious connotation. Botnets are used to perform DDoS attack, steal data, send spam, and the hacker can access the device and its connectivity. A botnet is controlled using command and control (c& c) software. Users cannot identify its presence in their systems. Botnet work on two kinds of models:…
Continue ReadingDenial of Service Attack
A denial-of-service attack(DOS attack) is a threat that switches off a machine or network, thereby making it inaccessible to its users. It is carried out by flooding more and more traffic towards the target or sending information to it so as to trigger a crash. In both cases, the DoS attack is deprived of intended users like employees, members, or account holders of the service or resource they expected. DoS attack does not result in any kind of theft or loss of crucial data, rather it cost the victim a huge chunk of money to stabilize and time. Methods of…
Continue Reading2019 Survey: Cyber Threats We Should Be Aware
It has been predicted that cyber attack will continue to rise in 2019. As per ISACA’s state of cybersecurity 2019 report, there are 3 main threat actors- cybercriminals (32%), hackers (23%), and non-malicious insider (15%). If we talk about this year’s 3 main attack vectors than phishing was found to be the most common type of cyber attack, whose percentage gone higher than the last year’s survey. The other 2 attack vectors were malware and social engineering. Despite the consistencies in threat vectors and actors, ISACA found that the frequency of attacks is likely to increase this year, as compared…
Continue ReadingFirewalls – The benchmark against threats
Firstly, you might be aware of a physical firewall that acts as a barrier against any person/activity to surpass it. In a similar way, a firewall in the digital world is defined as a protective barrier that protects your system from external cyber threats. A firewall is software whose job is to limit the intake of information by an external source. All the data whether entering or leaving passes via a firewall which can allow or block the data on a security basis. What exactly a firewall does? It prevents your systems and networks from unauthorized users. It monitors communication…
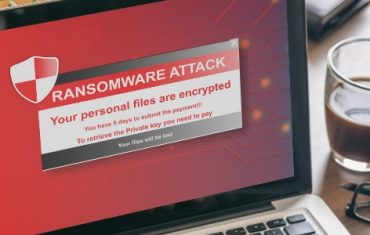
Continue ReadingRansomware Attacks and Healthcare
Ransomware is a threat which renders a system inoperable until a hacker is paid the ransom fee for providing the key to unlock the system. Irrespective of other cyber crimes, ransomware locks down the data. To infect the system with ransomware, attackers use social engineering techniques like phishing. Once the single system gets infected by ransomware, it may spread to the whole network of organization, encrypting files on both mapped and unmapped network drives. With the passage of time, it may even affect the organization’s backup files which are just next to impossible to restore the system. When the files…
Continue ReadingJackpotting – A recent cyber threat
Cybercriminals are leaving no stone unturned in making money by hacking various devices. There are many ways in order to carry out hacking. In this blog, I am going to shed light on another way which is called ‘Jackpotting’. This kind of hack is especially used for attacking ATM machines and to take all the cash from the ATM, there is a need for physical access to the dispensing device. In the recent past, the US encountered jackpotting in many areas. Diebold Nixdorf Inc. and NCR Corp., world’s largest ATM makers have warned US citizens that cybercriminals are targeting ATM’s…
Continue ReadingOnus of Cyber Threat Intel
We are enough knowledgeable about cybersecurity. Now, the question arises about those who are behind investing cyber threats i.e. Cyber threat intelligence. It is a domain of cybersecurity that gathers, evaluates, and analyzes data of all potential threats through various techniques. These cyber threats can be potentially dangerous and may harm your privacy. Thus, to keep these issues at bay, CTI came into power to cater to the needs of all the organizations by collecting information about these threats and making an effective strategy to eliminate them. CTI guarantees that any sort of security break can be counteracted. The essential…
Continue Reading