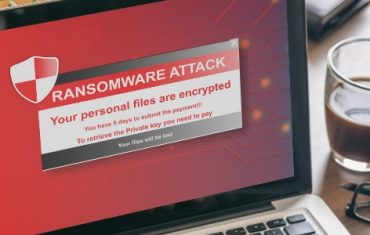
Ransomware is a threat which renders a system inoperable until a hacker is paid the ransom fee for providing the key to unlock the system. Irrespective of other cyber crimes, ransomware locks down the data. To infect the system with ransomware, attackers use social engineering techniques like phishing. Once the single system gets infected by ransomware, it may spread to the whole network of organization, encrypting files on both mapped and unmapped network drives. With the passage of time, it may even affect the organization’s backup files which are just next to impossible to restore the system. When the files…
Continue Readingnovalis
Jackpotting – A recent cyber threat
Cybercriminals are leaving no stone unturned in making money by hacking various devices. There are many ways in order to carry out hacking. In this blog, I am going to shed light on another way which is called ‘Jackpotting’. This kind of hack is especially used for attacking ATM machines and to take all the cash from the ATM, there is a need for physical access to the dispensing device. In the recent past, the US encountered jackpotting in many areas. Diebold Nixdorf Inc. and NCR Corp., world’s largest ATM makers have warned US citizens that cybercriminals are targeting ATM’s…
Continue ReadingOnus of Cyber Threat Intel
We are enough knowledgeable about cybersecurity. Now, the question arises about those who are behind investing cyber threats i.e. Cyber threat intelligence. It is a domain of cybersecurity that gathers, evaluates, and analyzes data of all potential threats through various techniques. These cyber threats can be potentially dangerous and may harm your privacy. Thus, to keep these issues at bay, CTI came into power to cater to the needs of all the organizations by collecting information about these threats and making an effective strategy to eliminate them. CTI guarantees that any sort of security break can be counteracted. The essential…
Continue ReadingEverything About Fake Antivirus Software
I am sure you all are well known about fake antivirus software. It is a common term these days that spread persistent threats on the system. It is a software which tends to act as the original software, show frequent pop-ups on the window regarding the infectious system. It can have negative effects over your system if you fall prey to this software. These pop-up messages appear as ‘your system is at risk’ or ‘antivirus scanning’. By looking at these messages, the user gets scared off and do whatever is needed to keep system risk free such as updating, installing,…
Continue ReadingWhat do you know about cybersecurity framework?
To build up a cross-segment cybersecurity system, US President has chosen the Department of Homeland Security (DHS), the National Institute of Standards and Technology (NIST), and the Department of Commerce (DOC). On April 3rd, 2013, the Special Assistant to the President for Cyber Security opened a board dialog in Washington, D.C. identified with Presidential Executive Order 13636. The motivation behind the board was to portray the procedure to be followed in building up a national standard. Congress had recently voted against a bill that contained the pith of what the Executive Order requires. Dependable government experts disclosed their general way…
Continue ReadingRole of Cybersecurity in Your Business
How seriously you take cybersecurity at your business? Is it something that you own or just a handover thing? Are you eager to make the effective use of this to protect and grow your business? To ensure high-end security, business continuously invests in security services. A small business can win a number of consumers by adopting this cybersecurity technique. With an active approach towards cybersecurity, a chain is formed as: SECURITY BUILD TRUST- When you start thinking cybersecurity as more than just protection, you’ll be surprised to see how investment brings a return. It is lucid that consumers’ priorities are…
Continue ReadingLatest Large Breaches
Do you have any idea about large breaches that affect well-established firms? These massive breaches come from an external source rather than an internal one. There are number of breaches that are coming in bulk and harming bigger firms, therefore they need to give priority on handling those attacks. Some biggest breaches that happened in recent years. Marriott:- Marriott’s Starwood hotel branch found a threat in 2018, which revealed the records of about 387 million guests with their names, gender, addresses, birthdates, and passport numbers. They did not know about this incident and it is estimated that this breach might…
Continue ReadingStrategies to save yourself from Social Engineering Attack
There are numerous types of social engineering attacks. One of my friends had been the victim of one of these attacks. She bore a great loss due to this threatening incident. As she came out of the loss, she found some ways by which one can avoid to become the victim of these crimes. 2FA/Multifactor authentication- One of the best ways to prevent hacking is the use of multifactor authentication where a hacker has to unlock numerous steps which become difficult and require long duration. Thereby, criminals may get frustrated and might not think of hacking. It is a good…
Continue ReadingHow much do you know about social engineering? – Part 2
In the previous, I have discussed social engineering and some of its attacks (Baiting, Phishing, Spear Phishing and Email hacking and Contact spamming). Today, I am going to discuss its remaining types. Scareware: – It is also known as deception software, rogue scanner software, or fraudware. In this attack, false reminders or threats are sent to victims system which upon clicking or installing impose serious threats and their systems get infected with malware. Example- while using the web, sometimes a popup is displayed regarding virus with a suggestion like to install software or you go to an infectious website. Pretexting:…
Continue ReadingHow much do you know about social engineering?
Often people get confused with the meaning of social engineering attack. Even I was not clear about it in the initial phases. Now, after gaining thorough knowledge, I find myself sufficient enough to aware you all about this attack. In an effective and simple language, this is a technique used by cyber attackers to target unsuspecting users; so that they may send their private data to them and infect their own computers with various threats by opening infected sites. Types of social engineering: Baiting – It increases the greed of a person by making false promises in order to steal…
Continue Reading